Edge Computing: Empowering Real-Time Data Processing
In today’s fast-paced digital world, real-time data processing is crucial, and edge computing is revolutionizing how we manage and process data.
Read morePOSTED BY
Ketan Rathod
From Boom to Moon: The Story Behind Bitcoin’s $92K Surge
The cryptocurrency world is buzzing with excitement as Bitcoin reaches an all-time high of $92,000 in November 2024. This milestone marks a pivotal moment, solidifying Bitcoin’s status as a dominant asset class while sparking discussions about its future trajectory.
Read morePOSTED BY
Shivi Sharma
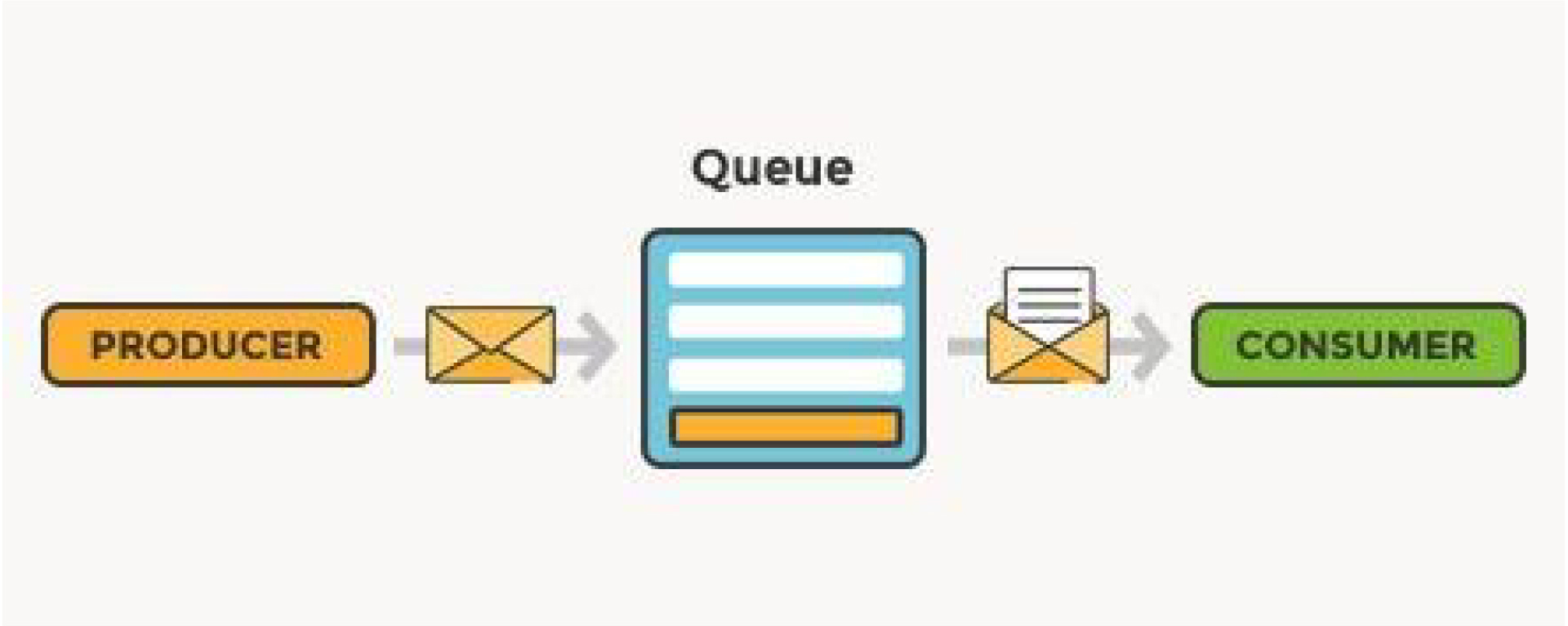
Overvview Of Messaging Queue
Messaging queue is a process of sharing the data asynchronously between two or more services. The software that puts messages into a queue is called a message producer. The software that retrieves messages from the queue is called a message consumer.
Read morePOSTED BY
Hetul Parmar
The Rise of AI in Project Management: Transforming Efficiency and Success
Project management has always been a balancing act of tasks, deadlines, and team coordination. But with the rise of AI-powered tools, this balancing act is getting a major upgrade. AI project management tools are reshaping how we plan, execute, and deliver projects. From automating routine tasks to predicting project risks, these tools are a game-changer…
Read morePOSTED BY
Geetanjali Padhy
Artificial Intelligence and Automation: How AI Can Streamline Operations and Improve Customer Experiences
The world of technology is in a constant state of evolution, with breakthroughs and innovations reshaping industries and our daily lives. Among the most intriguing and potentially transformative of these advancements is quantum computing. While still in its nascent stages, quantum computing promises to revolutionize everything from ..
Read morePOSTED BY
Freddie Master
What is Database Sharding?
The world of technology is in a constant state of evolution, with breakthroughs and innovations reshaping industries and our daily lives. Among the most intriguing and potentially transformative of these advancements is quantum computing. While still in its nascent stages, quantum computing promises to revolutionize everything from ..
Read morePOSTED BY
Anjana Gojiya
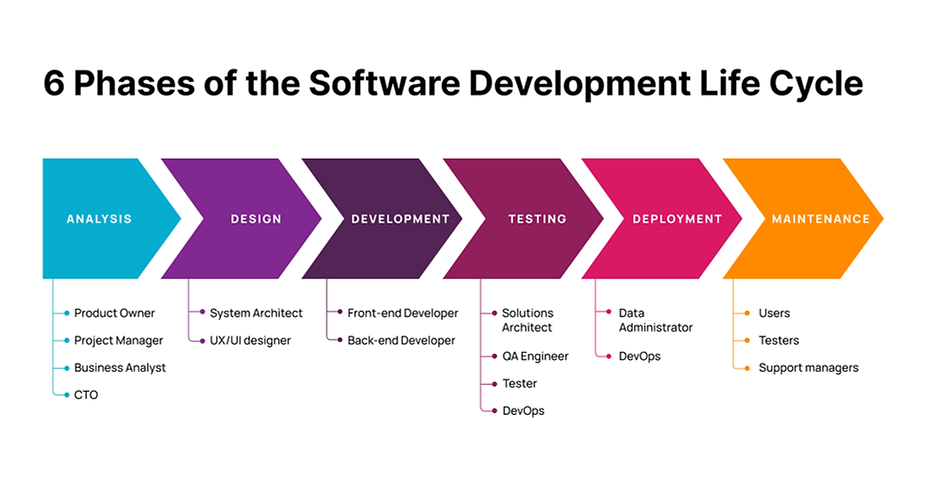
In-Depth Look at Software Engineering Phases
The world of technology is in a constant state of evolution, with breakthroughs and innovations reshaping industries and our daily lives. Among the most intriguing and potentially transformative of these advancements is quantum computing. While still in its nascent stages, quantum computing promises to revolutionize everything from ..
Read morePOSTED BY
Prince Narola
Serverless Computing: Future of Scalable Applications
The world of technology is in a constant state of evolution, with breakthroughs and innovations reshaping industries and our daily lives. Among the most intriguing and potentially transformative of these advancements is quantum computing. While still in its nascent stages, quantum computing promises to revolutionize everything from ..
Read morePOSTED BY
Jainam Doshi
Unlocking the Quantum Frontier: The Future of Quantum Computing
The world of technology is in a constant state of evolution, with breakthroughs and innovations reshaping industries and our daily lives. Among the most intriguing and potentially transformative of these advancements is quantum computing. While still in its nascent stages, quantum computing promises to revolutionize everything from ..
Read morePOSTED BY
Henil Mamaniya
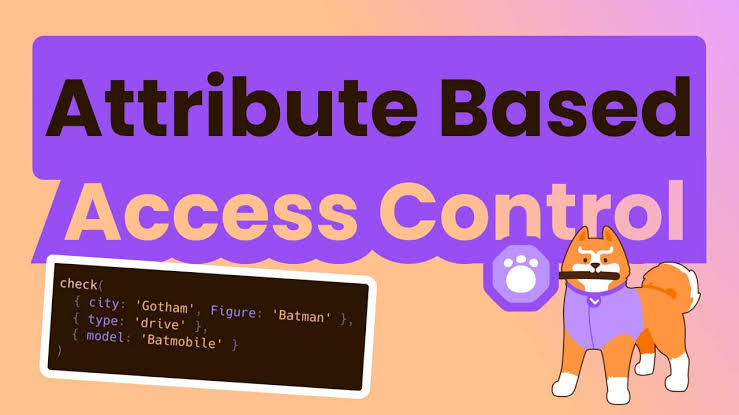
Attribute-Based Access Control (ABAC)
In the ever-evolving landscape of cybersecurity, controlling access to resources is paramount. Two of the most widely used access control models are Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC). Unlike traditional models like RBAC, which rely solely on predefined roles, ABAC evaluates attributes associated with users, resources, and the environment to determine access…
Read morePOSTED BY